Last updated on July 9th, 2025 at 10:55 pm
In 2025, cybersecurity threats are at an all-time high, making robust authentication methods more critical than ever. Traditional two-factor authentication (2FA) methods, such as SMS and email-based OTPs, are increasingly vulnerable to phishing, SIM swapping, and man-in-the-middle attacks. To counter these risks, voice-based OTPs (One-Time Passwords) are emerging as a revolutionary solution, offering enhanced security, accessibility, and efficiency. Two-factor authentication (2FA) has become a crucial security measure in today’s digital world. By adding an extra layer of protection, it helps ensure that only authorized individuals gain access to sensitive information or accounts. However, traditional 2FA methods have their limitations. This can be overcome with the emergence of a new and innovative approach called Voice-Based OTP.
Another significant advantage of Voice-Based OTP lies in its ability to bridge the digital divide. Unlike SMS or email OTPs that require stable internet connectivity or advanced devices, Voice OTPs can be delivered through simple phone calls, making them accessible to users in remote or underserved regions. This not only enhances security but also ensures inclusivity, allowing a broader population to benefit from strong authentication methods. With platforms like FreJun, businesses can seamlessly integrate Voice OTP solutions into their systems, ensuring fast, reliable, and secure verification experiences for users across the globe.
How Does Voice OTP Improve 2FA Security and Access?
1, Enhanced Accessibility: Voice OTP Works Well For Users With Visual Impairments Or Limited Access To Text-Based Devices.
2. Network Flexibility: Unlike SMS, Voice OTP Can Be Delivered Over VoIP, Making It Reliable Even In Areas With Poor Mobile Coverage.
3. Lower Risk Of SIM Swap Attacks: Voice OTPs Are Less Vulnerable To SIM Swap Fraud Compared To SMS OTPs.
4. Global Reach: Services Like FreJun Allow Voice OTP Delivery Across Countries Without Dependence On Local Telecoms.
5. Automation Ready: Voice OTP Can Be Easily Integrated With Automated Systems And CRM Tools For Seamless Authentication.
What is Two-Factor Authentication
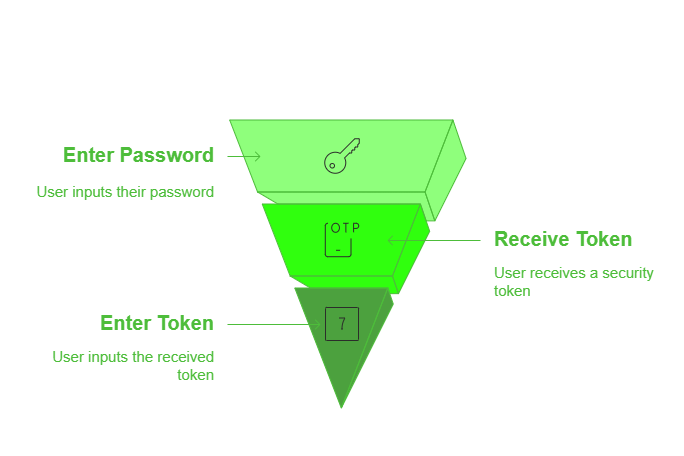
In order to grasp the significance of Voice-Based OTP, it’s important to first understand the basics of two-factor authentication. Simply put, 2FA is a security process that requires users to provide two separate forms of identification before accessing their accounts. Typically, these are something the user knows (such as a password) and something the user has (such as a physical device).
Implementing two-factor authentication adds an extra layer of security. It does this by making it more difficult for hackers to gain unauthorized access to accounts, even if they manage to obtain the user’s password through methods like phishing or keylogging.
The Basics of Two-Factor Authentication
Two-factor authentication follows the principle of “something you know” and “something you have.” The “something you know” factor is typically a password or PIN that only the user should have access to. This password or PIN acts as the first line of defense, ensuring that only authorized individuals can access the account.
The “something you have” factor is usually a physical device. It could be a smartphone or a hardware token, that generates time-based one-time passwords. These devices are designed to be in the possession of the user and are used to verify their identity during the authentication process.
With the combination of these two factors, even if someone discovers the user’s password, they would still need the physical device to gain access to the account. This significantly reduces the risk of unauthorized access and enhances the overall security of the account.
The Role of Two-Factor Authentication in Cybersecurity
Two-factor authentication plays a critical role in enhancing cybersecurity. With the increasing number of cyber threats and sophisticated hacking techniques, relying solely on passwords for account security is no longer sufficient. Passwords can be easily compromised through various means, but using an enterprise password manager alongside two-factor authentication significantly reduces the risk of unauthorized access and data breaches.
By requiring users to provide a second form of identification, two-factor authentication provides an additional layer of protection against unauthorized access. This helps prevent identity theft, data breaches, and other security issues that can have severe consequences for individuals and organizations.
Implementing two-factor authentication is particularly crucial for organizations that deal with sensitive data, such as financial institutions, healthcare providers, and government agencies. It adds an extra level of security, ensuring that only authorized individuals can access sensitive information and reducing the risk of data breaches.
In an increasingly digital world, where cyber threats are on the rise, implementing 2FA has become a necessity for individuals and organizations alike. It is a proactive measure that enhances security and protects against the ever-evolving landscape of cybercrime.
The Limitations of Traditional Two-Factor Authentication
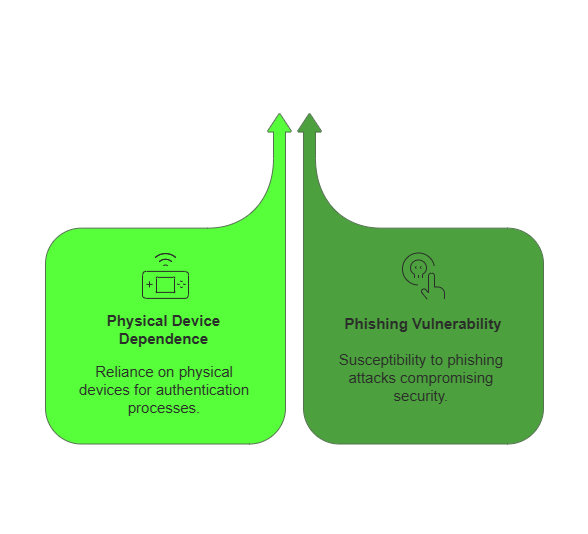
While traditional 2FA methods have proven to be effective in improving account security, they do come with their limitations. Let’s take a closer look at two of the major drawbacks:
1. Dependence on Physical Devices
One of the main limitations of traditional 2FA is its reliance on physical device. This could be hardware tokens or smartphone apps. Users often need to carry these devices with them at all times, which can be inconvenient and increase the risk of loss or theft. Additionally, issuing and managing physical devices can be costly for organizations.
Moreover, relying solely on physical devices for authentication can be problematic in many situations. One instance could be when users don’t have immediate access to their devices, such as when traveling or in case of device malfunction.
Imagine a scenario where you’re on a business trip and you accidentally leave your hardware token at home. You urgently need to access your account, but without the physical device, you’re locked out. This dependency on physical devices can cause significant inconvenience and frustration for users.
Furthermore, the cost of providing hardware tokens or smartphone apps to all users within an organization can be substantial. This financial burden may deter some organizations from implementing traditional 2FA methods, leaving their accounts vulnerable to attacks.
2. Vulnerability to Phishing Attacks
Phishing attacks remain a widespread threat, and traditional 2FA methods are not immune to them. Cybercriminals can deceive users by creating fake websites or sending phishing emails. This can trick individuals into revealing their passwords and entering the generated one-time passwords on bogus pages. This vulnerability undermines the effectiveness of traditional 2FA methods.
Imagine receiving an email that appears to be from your bank, asking you to verify your account by clicking on a link and entering your credentials. You unknowingly fall victim to a phishing attack and enter your information on a fraudulent website. Even if you have two-factor authentication enabled, the cybercriminals can intercept the generated one-time password and gain access to your account.
This vulnerability highlights the importance of user awareness and education in recognizing and avoiding phishing attempts. However, even with proper training, some users may still fall victim to sophisticated phishing techniques, putting their accounts at risk.
These limitations highlight the need for a more secure and convenient form of two-factor authentication. Organizations and individuals alike must continue to explore and adopt innovative solutions that address these drawbacks, ensuring the highest level of account security.
What is Voice-Based OTP
Voice-Based OTP is a groundbreaking approach to two-factor authentication that addresses the limitations of traditional methods. It leverages the power of voice recognition technology to offer enhanced security and accessibility.
In today’s digital age, where cyber threats are becoming increasingly sophisticated, it is crucial to implement robust security measures to protect sensitive information. Traditional methods of authentication, such as passwords or physical tokens, have proven to be vulnerable to various attacks, including phishing and brute force attacks. Voice-Based OTP offers a more secure alternative by utilizing the unique characteristics of an individual’s voice.
By incorporating voice recognition technology into the authentication process, Voice-Based OTP provides an additional layer of security that is difficult to replicate or manipulate. This method not only enhances security but also offers convenience and accessibility to users, as they can authenticate themselves using their voice, eliminating the need for physical devices or remembering complex passwords.
Key Advantages of Voice OTP Over Traditional OTP Methods
| Feature | SMS OTP Challenges | Voice OTP Solution |
| Security | Prone to SIM swap and interception | Encrypted voice transmission reduces hacking risk |
| Delivery Reliability | Delayed or undelivered due to network congestion | Higher success rate, works on unstable networks |
| User Accessibility | Requires reading and typing | Hands-free, useful for visually impaired users |
| Scalability for Businesses | Limited to text-based delivery | AI-driven, supports multi-channel authentication |
| Regional Language Support | Restricted to SMS-supported languages | Can be spoken in multiple languages dynamically |
| Integration with AI | Limited automation capabilities | Seamless AI integration, like FreJun’s smart authentication |
What is Voice-Based OTP?
Voice-Based OTP is a method of authentication that utilizes the unique characteristics of an individual’s voice to verify their identity. Instead of relying on physical devices or passcodes, Voice-Based OTP uses spoken words or phrases as a means of authentication.
The process begins when a user requests access to an account or performs a transaction. They are prompted to provide a specific voice command or answer a predetermined question. The voice sample is then compared to the user’s pre-registered voice pattern to authenticate their identity.
Each person’s voice has distinct qualities, including pitch, tone, accent, and pronunciation, which make it unique. Voice-Based OTP leverages these characteristics to create a reliable and secure authentication method.
By using voice as a means of authentication, Voice-Based OTP offers several advantages over traditional methods. It eliminates the risk of password theft or keylogging attacks, as there is no physical element that can be compromised. Additionally, it provides a more user-friendly experience, as users can authenticate themselves simply by speaking, without the need to remember complex passwords or carry physical tokens.
Further Reading: The Ultimate Guide to Call Recording Software for Sales Teams
How Voice-Based OTP Enhances 2FA Security (2025)
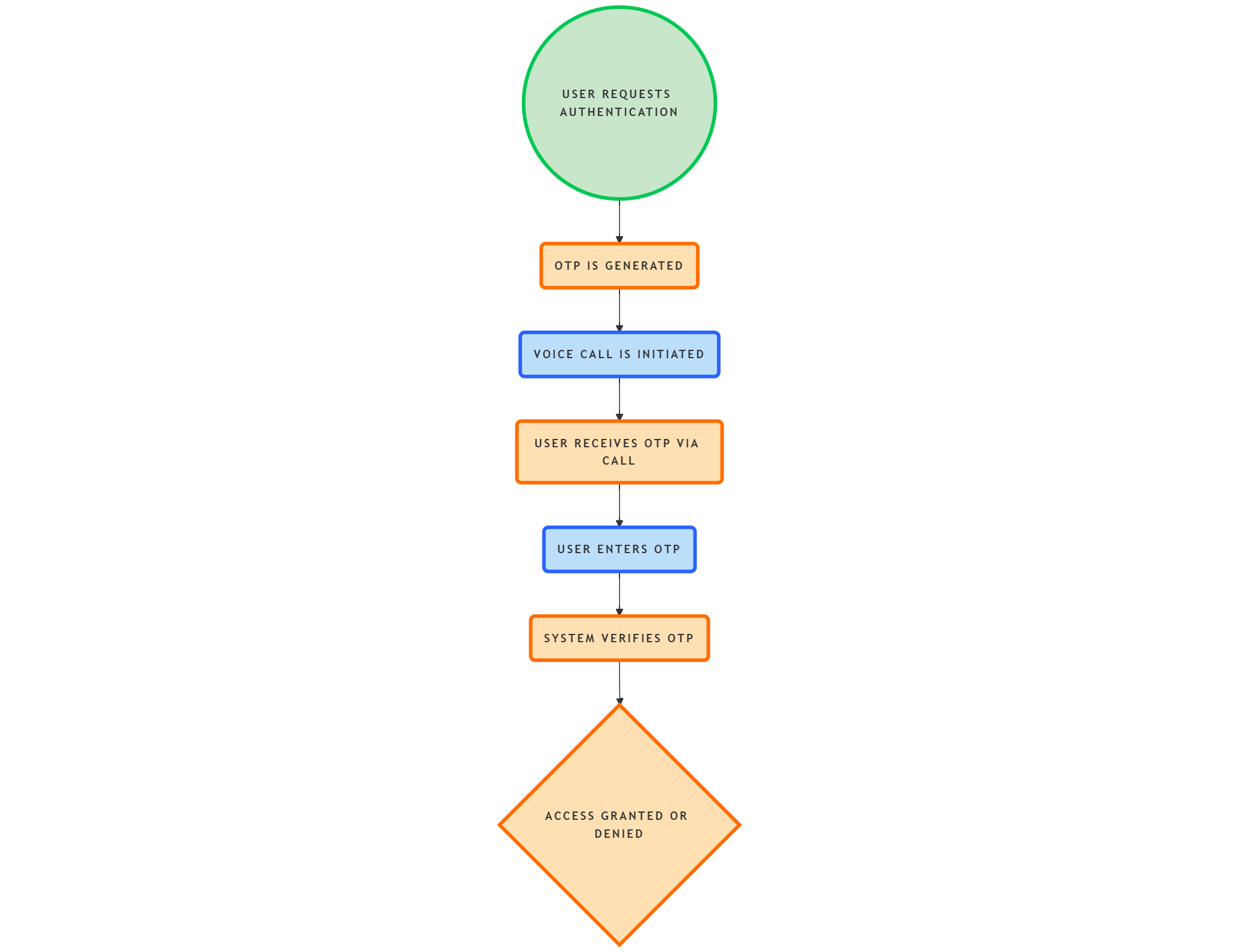
How Does Voice-Based OTP Work?
Voice-Based OTP relies on advanced voice recognition algorithms that analyze various factors, such as pitch, tone, and accent, to create a unique voice profile for each user. This profile is securely stored and used for future authentication purposes.
When a user initiates the authentication process, their voice is recorded and compared against their stored profile. If the voice matches, access is granted. This innovative method adds an extra layer of security by authenticating users based on their unique voice patterns, making it difficult for impostors to gain unauthorized access.
The voice recognition algorithms used in Voice-Based OTP are designed to adapt to changes in an individual’s voice over time. Factors such as age, illness, or emotional state can affect a person’s voice, but the system can still accurately authenticate the user by accounting for these variations.
Furthermore, Voice-Based OTP can be integrated into various platforms and devices, including mobile applications, call centers, and IoT devices. This flexibility makes it a versatile authentication solution that can be tailored to different use cases and industries.
It is worth noting that Voice-Based OTP is not without its limitations. Factors such as background noise, poor audio quality, or voice impersonation attempts can affect the accuracy of authentication. However, continuous advancements in voice recognition technology are constantly improving the reliability and security of Voice-Based OTP.
In conclusion, Voice-Based OTP is a cutting-edge authentication method that offers enhanced security, convenience, and accessibility. By harnessing the unique characteristics of an individual’s voice, it provides a reliable and secure means of verifying identity. As the digital landscape continues to evolve, Voice-Based OTP is poised to play a significant role in ensuring secure transactions and protecting sensitive information.
Advantages of Voice-Based OTP
Voice-Based OTP offers several advantages over traditional 2FA methods, making it a revolutionary approach to authentication:
1. Enhanced Security Measures
By utilizing the unique characteristics of an individual’s voice, Voice-Based OTP provides a highly secure method of authentication. Voice patterns are difficult to replicate. This makes it incredibly challenging for impersonators or hackers to gain unauthorized access to an account.
The use of voice recognition technology adds an additional layer of protection. This makes Voice-Based OTP an ideal solution for industries that handle sensitive information, such as financial institutions and healthcare organizations.
2. User Convenience and Accessibility
Voice-Based OTP offers a convenient and user-friendly authentication experience. It eliminates the need for physical devices, such as tokens or smartphones, which are easily misplaced or forgotten. Users simply need to speak their predetermined voice command in order to authenticate their identity.
This method also provides accessibility benefits. For instance, individuals with visual impairments or physical disabilities that hinder device usage can still authenticate using Voice-Based OTP.
Implementing Voice-Based OTP
Integrating Voice-Based OTP into existing systems requires careful planning and a thorough understanding of the organization’s security requirements. Here are two key considerations:
1. Integration with Existing Systems
Before implementing Voice-Based OTP, organizations need to ensure that their systems and applications can seamlessly integrate with the voice recognition technology. This may involve working closely with technology providers or developing in-house solutions that can handle voice authentication securely.
Compatibility with existing systems is crucial to avoid disruptions and ensure a smooth transition to the new authentication method.
2. User Onboarding and Education
A successful implementation of Voice-Based OTP relies on effective user onboarding and education. Organizations must clearly communicate the benefits and procedures of the new authentication method to their users. This includes explaining how they can enroll their voice patterns and providing guidance on how to perform the authentication process smoothly.
Furthermore, organizations should emphasize the importance of protecting their voice samples. Also they should highlight the security measures in place to safeguard users’ personal information.
Conclusion
Voice-based OTP is revolutionizing the way we approach two-factor authentication by offering enhanced security, accessibility, and convenience. As cyber threats evolve, businesses and individuals must adopt innovative authentication solutions to stay ahead of attackers. With its ability to counter phishing, SIM swapping, and poor network challenges, voice-based OTP is set to become a mainstream security standard in 2025.
Voice-Based OTP has the potential to revolutionize two-factor authentication, offering enhanced security measures and user convenience. By eliminating the need for physical devices and capitalizing on voice recognition technology, it provides a more secure and accessible method of authentication.
As organizations strive to protect their sensitive information and users’ accounts, Voice-Based OTP is an innovative solution worth considering. It not only strengthens security but also provides a seamless user experience, ultimately revolutionizing the way we authenticate our digital identities.
Further Reading: Voice OTP vs SMS OTP: Which is more secure?
Frequently Asked Questions
Voice OTP Is A Security Method That Delivers A One-Time Password Through A Voice Call Instead Of SMS Or Email.
Voice OTP Reduces The Risk Of SIM Swap And Message Interception, Making It A More Secure Alternative.
Yes, Platforms Like FreJun Support Global Voice OTP Delivery Using VoIP, Making It Ideal For Remote Or International Users.
Absolutely. Voice OTP Offers An Extra Layer Of Security And Is Widely Used In Banking, FinTech, And Secure Transactions.
Using FreJun’s API, You Can Easily Connect Voice OTP Functionality With Your Platform’s Backend System.
Costs Vary By Region, But FreJun Offers Affordable Packages That Balance Cost And Security Efficiently.
Yes, Platforms Like FreJun Support Global Voice OTP Delivery Using VoIP, Making It Ideal For Remote Or International Users.
Subhash is the Founder of FreJun, the global call automation platform. With 8+ years of entrepreneurial experience, FreJun was established to help customers with their voice communication needs. The goal of FreJun is to develop cutting edge technology and solutions to help customers.
